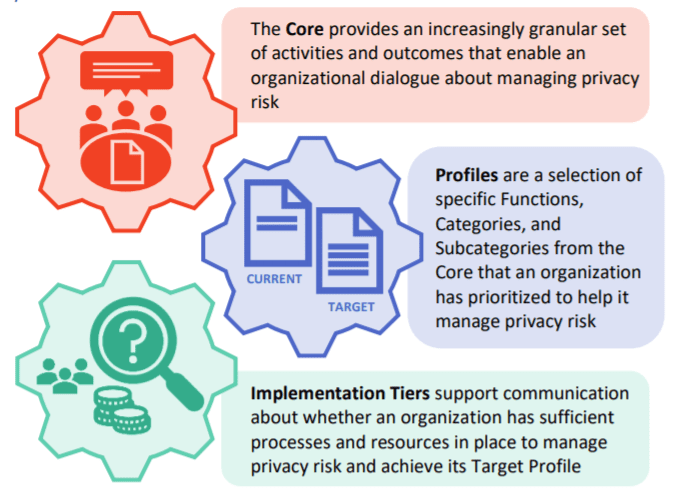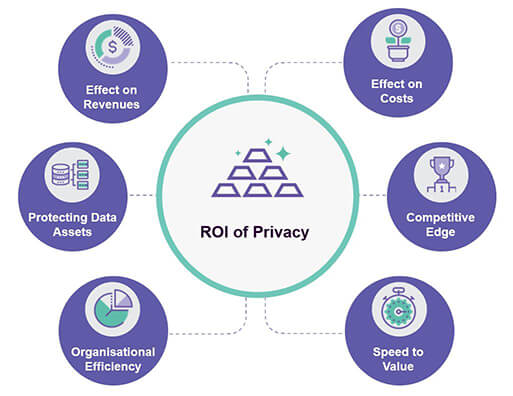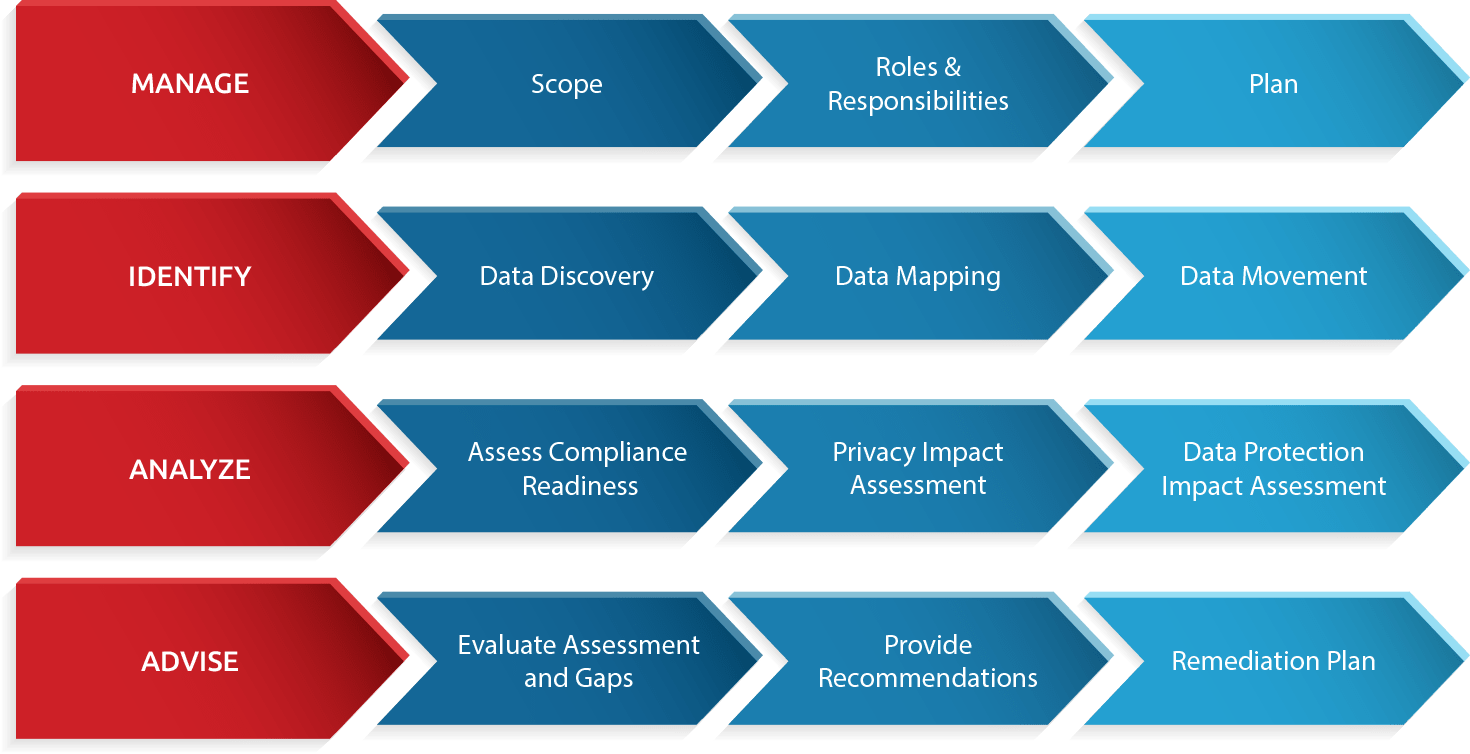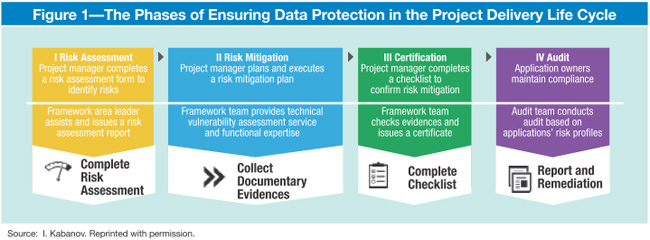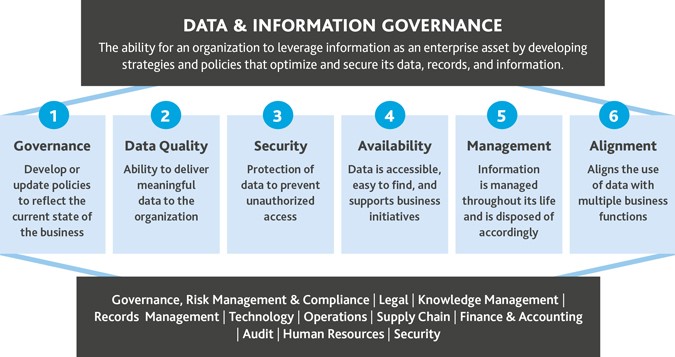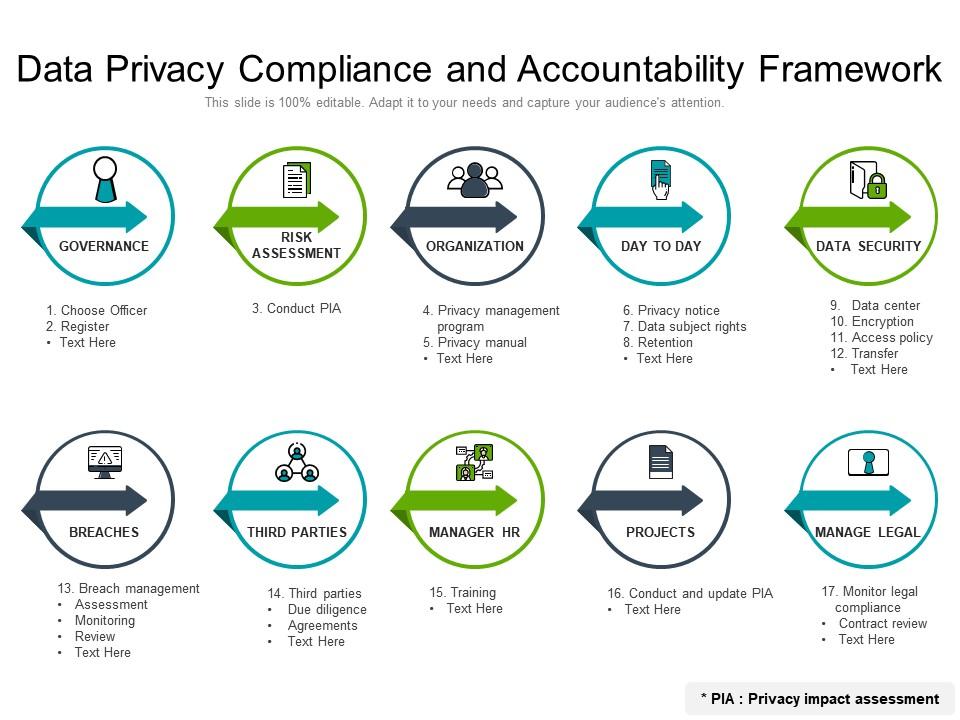
Data Privacy Compliance And Accountability Framework | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
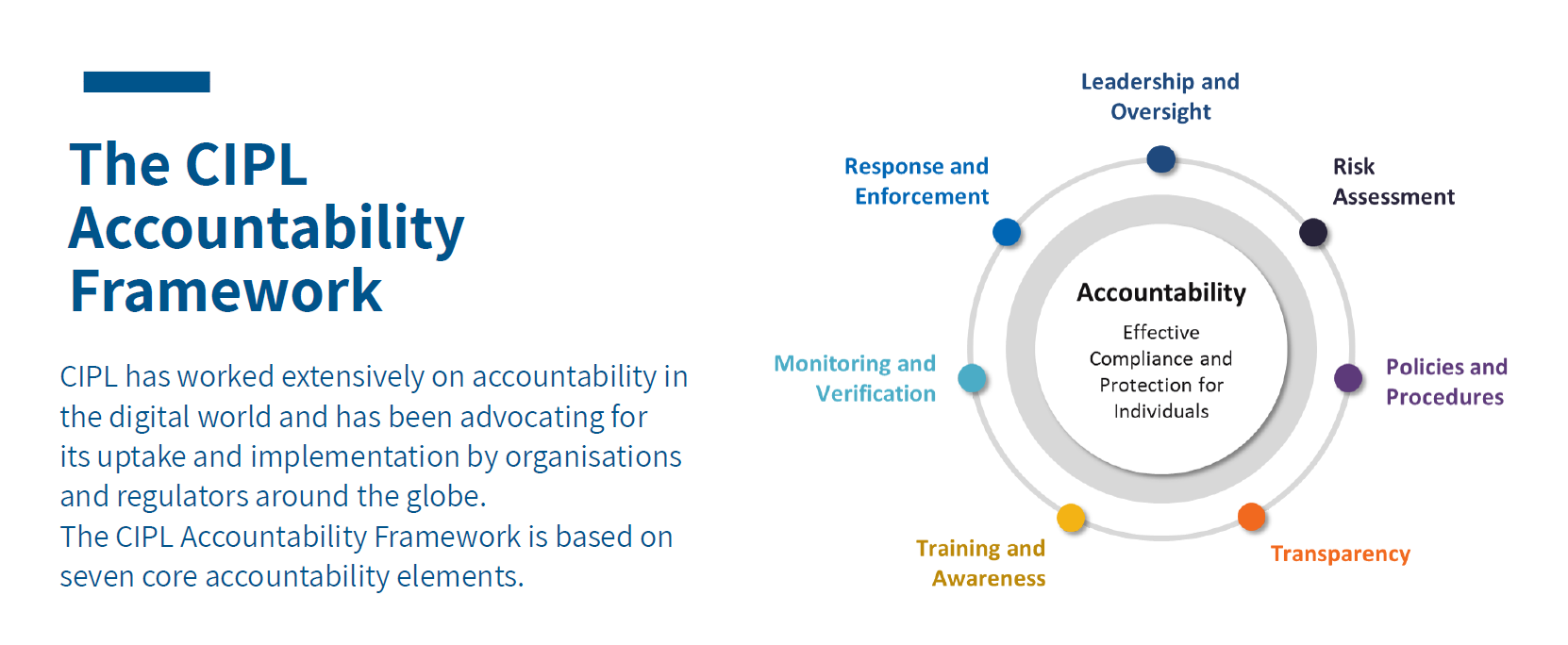
CIPL Releases Report on Effective Data Privacy Accountability | Privacy & Information Security Law Blog

Inference Privacy Framework. S = sensor data, C = context state, I =... | Download Scientific Diagram

TrustArc Privacy & Data Governance Accountability Framework – TrustArc The Leader in Privacy Management Software

AUNH Systems - Build a Privacy Program Your personal data is showing. A common assumption is that security and privacy are one and the same. Security's role is to protect and secure
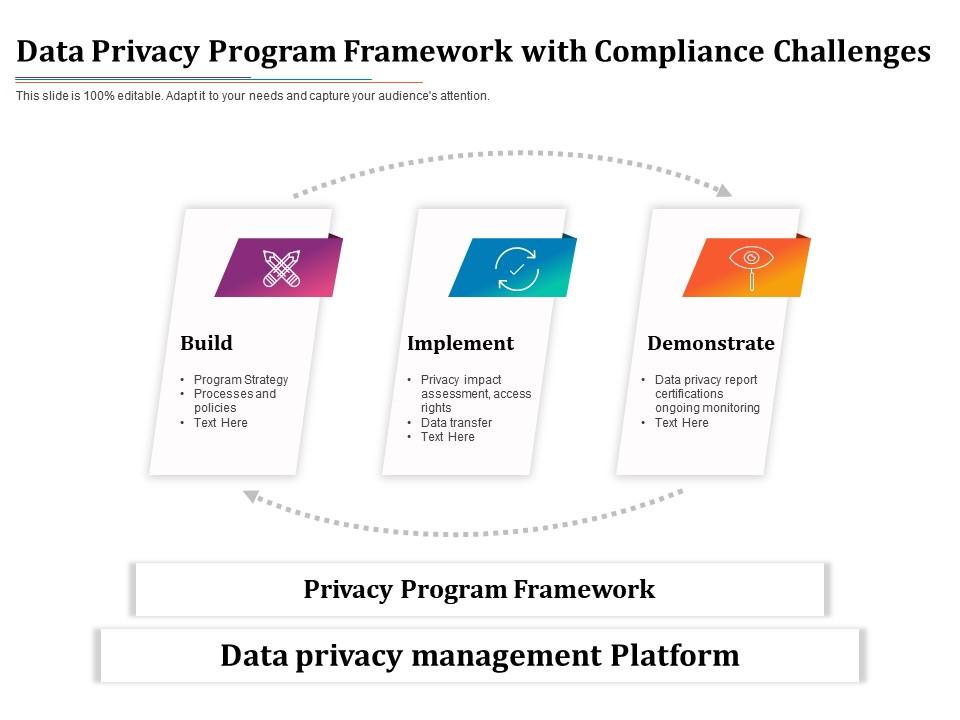
Data Privacy Program Framework With Compliance Challenges | Presentation Graphics | Presentation PowerPoint Example | Slide Templates